Seeking the Best IT Support? 4 Signs It’s Time to Switch Providers

Discover key signs it’s time to switch IT providers. Learn what great service looks like to ensure you’re getting the best IT support for your business.
How to Check a Link’s URL Without Clicking It
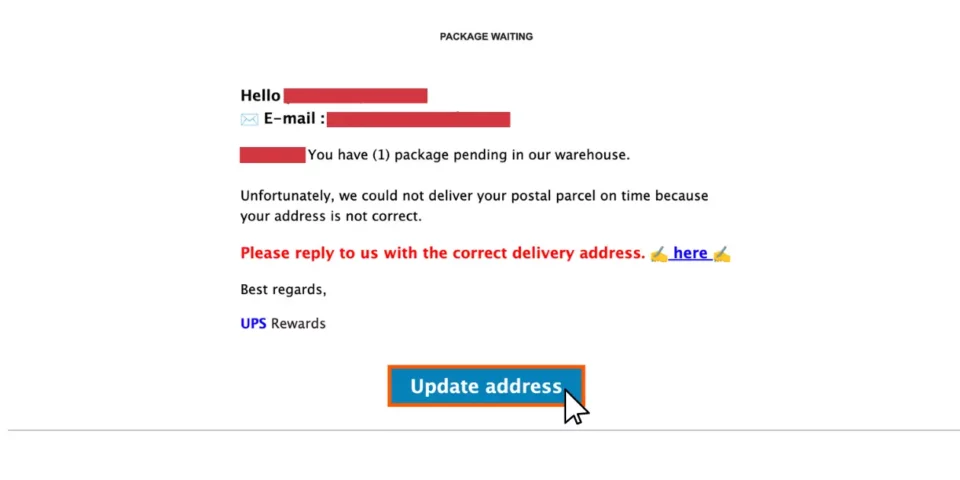
Learn how to protect yourself from risky phishing links with this helpful Tech Tip: discover how to check a link’s URL destination without clicking on it.
How to Recognize Business Email Compromise Attacks

Learn how to recognize business email compromise attacks, their warning signs, and different BEC attack examples.
Network Assessments: The Why, What, & How to Identify Weaknesses
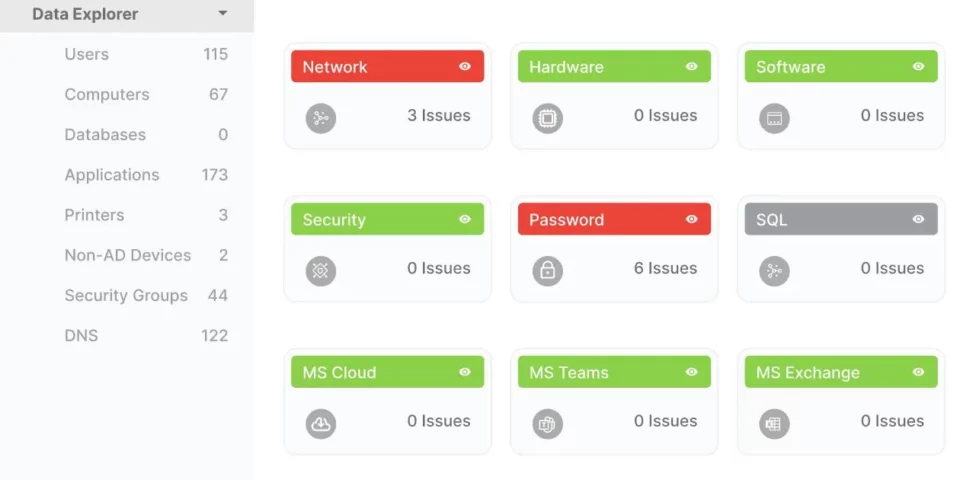
In this blog we’ll cover the importance of network assessments, how it’s conducted, the insights you’ll receive, and how to request one.
Vape Sensors: Your New Safety Tool to Prevent Vaping in Schools

This blog discusses the real dangers around vaping in teens, the struggle to prevent vaping in schools, and ways vape sensors can put a stop to it.
