How to Recognize Business Email Compromise Attacks

Learn how to recognize business email compromise attacks, their warning signs, and different BEC attack examples.
5 Genetec Solutions That You Might Not Know About

Learn about 5 Genetec security solutions, including Genetec access control, ALPR, & more, that you should know about for your unified security platform.
Network Assessments: The Why, What, & How to Identify Weaknesses
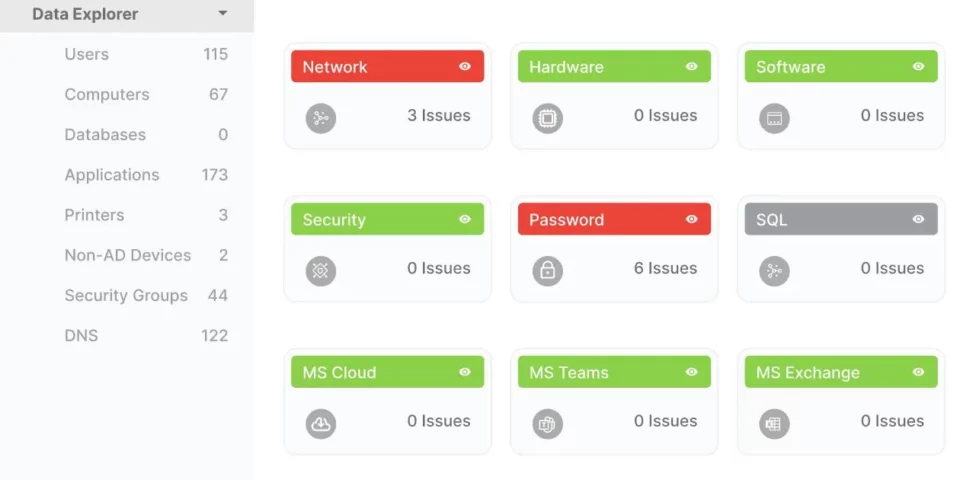
In this blog we’ll cover the importance of network assessments, how it’s conducted, the insights you’ll receive, and how to request one.
Vape Sensors: Your New Safety Tool to Prevent Vaping in Schools

This blog discusses the real dangers around vaping in teens, the struggle to prevent vaping in schools, and ways vape sensors can put a stop to it.
How to Recycle Computer Hardware: Protect Yourself & The Planet

Don’t discard old computer hardware by throwing it out. Instead, consider destroying or recycling to ensure important data is wiped off and limit e-waste.
