How to Avoid Phishing Emails: Spot Phishing Signs
Avoid evolving phishing scams
Phishing scams are constantly evolving using sophisticated tactics to exploit the trust and curiosity of small and medium-sized businesses. One recent scheme uses seemingly genuine inquiries to trick businesses into costly mistakes. By understanding how these scams operate, you can protect your company and its resources. Let’s break down how this particular scam works and how you can avoid falling victim.
Watch for these phishing signs
Scammers are getting creative, posing as representatives from well-known companies and leveraging your website’s contact form to initiate fraudulent communication.
Look for these phishing signs:
- They appear legitimate by expressing interest in purchasing large quantities of your products.
- This enticing offer is designed to gain your trust and lure you in with the promise of a lucrative deal.
Be aware, always verify the authenticity of inquiries, and watch for red flags to protect your business.
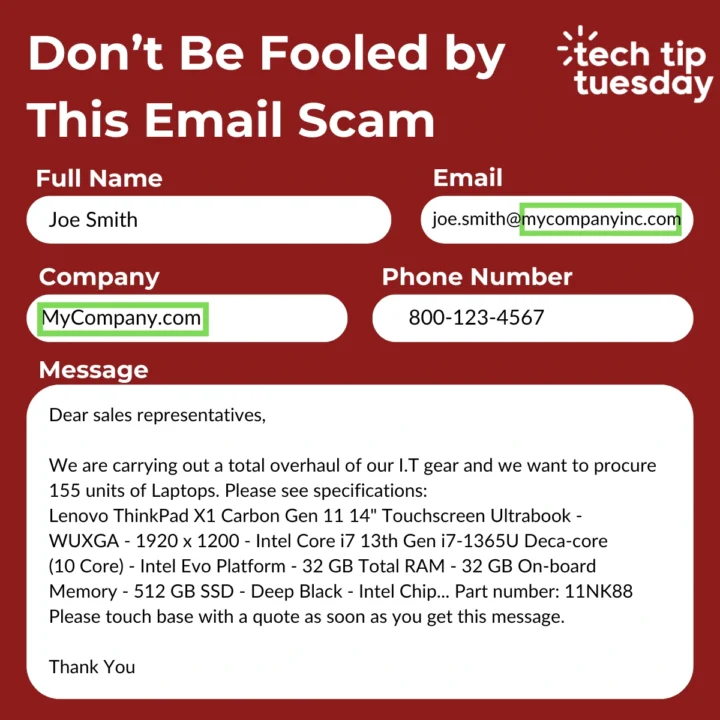
Stay alert for subtle discrepancies in email addresses. Scammers often use lookalike domains, such as “mycompanyinc.com,” to imitate the legitimate “mycompany.com.” They may also include a functional but unrelated phone number to appear credible.
What to do with phishing emails
Take these steps to verify the inquiry:
- Perform a quick Google search for the company’s official contact details.
- Reach out to the company directly to confirm the request.
This simple action can lead to two outcomes:
- You uncover a genuine opportunity—great news!
- You alert the real company, helping them address unauthorized use of their name.




