How to Protect Your Online Privacy on Social Media
Understanding Social Media Privacy
Let’s talk about the concept of online privacy, especially social media privacy. It’s important to protect personal information from being exploited. By being mindful of what you share, you can prevent identity theft and social engineering attacks. Regularly reviewing and adjusting your privacy settings helps maintain control over your digital footprint and ensures your online privacy remains secure.
Consider the post below.
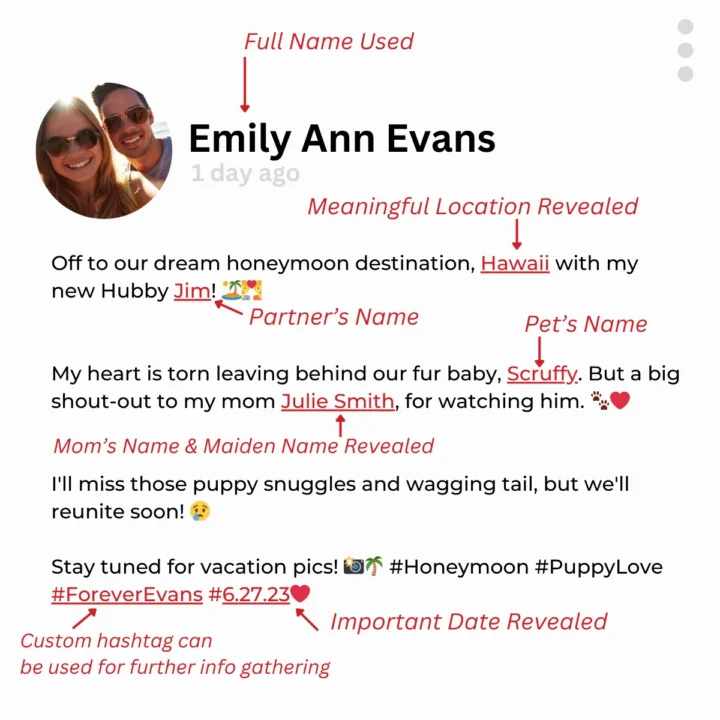
At first glance, the post might seem harmless. However, it reveals names, dates, locations, and more, which cybercriminals could exploit.
Online Privacy Tips
It’s important to recognize the risks associated with sharing too much online. Here are some mindful tips to help you protect your personal information:
- Use a middle initial, your first name and last initial, or just your last name instead of your full name on social media.
- Restrict post and photo visibility to your connections only.
- Regularly review and adjust your privacy settings.
- Be cautious of duplicated friend accounts; one might be genuine, while the other could be an imposter.
- Avoid listing important dates, like anniversaries or birthdays, in your bio, as even non-connections can see this information.
Could you be sharing too much on social media? Read our full blog to learn more.