What are business email compromise attacks?
Cybercriminals employ various tactics to deceive unsuspecting individuals into falling victim to business email compromise attacks, also known as BEC attacks. These deceptive schemes often involve tricking individuals into transferring funds or sharing sensitive information. It’s crucial to prioritize education and awareness when it comes to protecting against BEC attacks. In this blog, we will review BEC attack examples that provide insight into how these schemes operate and how to defend against them.
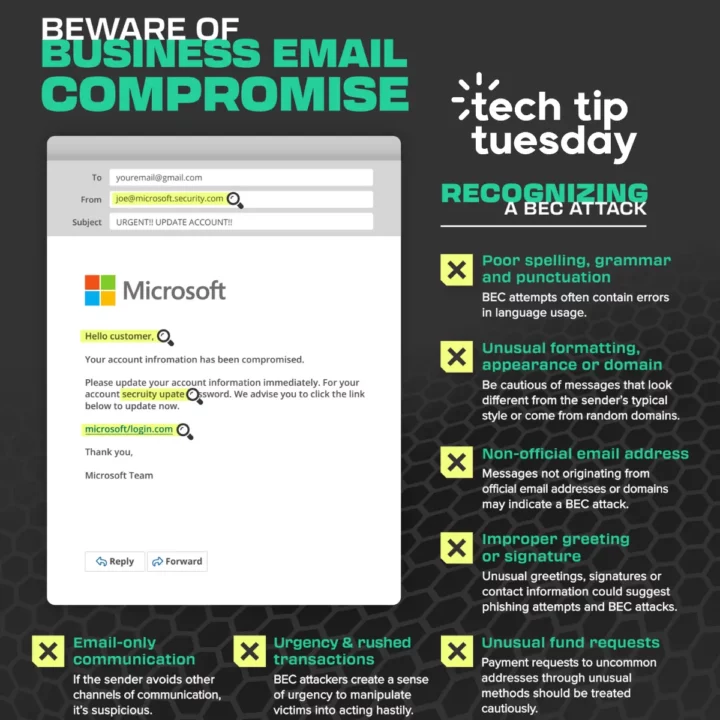
One effective way to prevent sophisticated phishing attacks, such as BEC, is to be able to identify them promptly. Fortunately, BEC exploits typically exhibit common red flags that can serve as indicators.
By familiarizing yourself with these common telltale signs of BEC attacks, you can better protect yourself and your organization from falling victim to these malicious schemes. Remember, education and awareness are key in the ongoing battle against cybercrime. Stay informed, stay vigilant, and keep your cyber defenses strong.
BEC attack examples and warning signs
✔️ Spelling, grammar, and punctuation errors
✔️ Odd formatting
✔️ Unofficial email addresses
✔️ Inappropriate greetings or signatures
✔️ Strange money requests
✔️ Urgency pressure
✔️ Relying on only email for communication
Enhance your cyber defense against business email compromise attacks
Feeling unsure about where to start in building a cyber-ready workforce? Begin your journey with Prime Secured today! Our tailored training programs cover threats like phishing scams and business email compromise attacks. With cutting-edge technologies and solutions, our team of experts has everything your business needs to protect itself and stay ahead of cyber threats.




