We Are all Targets for A Cyber Threat
We all share the same vulnerability of becoming the next cyber victim, whether you are targeted individually or as an organization. It’s important to be overly prepared, which is why we are bringing you another topic around cybersecurity (it is our specialty, after all). Today, we want to discuss two key themes: first, we are going to share why your business needs to be prepared for a cyber incident- if you aren’t already aware, and secondly, how to enhance your cyber incident response plan.
Let’s cover the basics, the following are some examples of common types of incidents to be aware of:
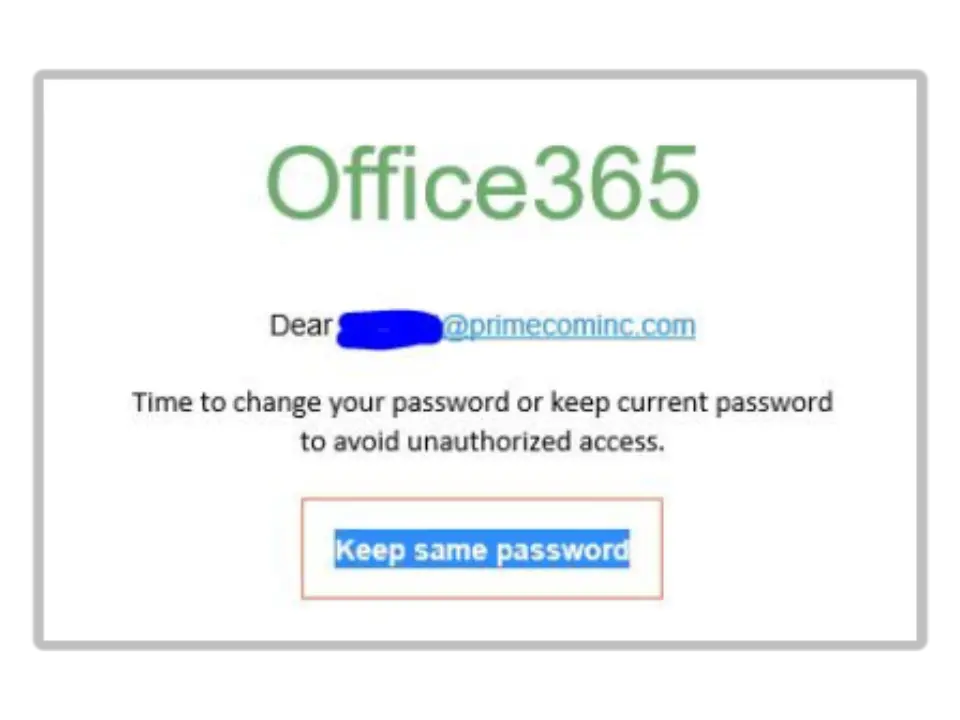
Phishing
Phishing is an online scam where criminals send emails or instant messages falsely claiming to be from a legitimate organization. These messages typically contain links to bogus websites designed to steal your personal information, such as your login credentials or credit card number. Phishing attacks can be challenging to detect because scammers use familiar logos and language to dupe their victims. With technology like AI, they have become increasingly believable, here are further resources to educate and protect yourself:
Denial-of-service
A denial-of-service attack makes a computer or other service inaccessible to users. These attacks are carried out by flooding the victim’s computers or network with requests, rendering it unable to respond to legitimate traffic or causing it to crash. Such attacks can be excessively disruptive and can result in significant financial losses.
Ransomware
Ransomware- the big one. A ransomware attack is a cyberattack through which hackers encrypt a victim’s data and demand a ransom to decrypt it. Encryption is the process of transforming readable data into an unreadable format. This is done using a key, which is a piece of information that controls the transformation. Only the same key can convert the unreadable format to readable data or decrypt it.
These attacks can be incredibly detrimental to individuals and organizations since they frequently lead to loss of data or money.
We have a handful of resources dealing with ransomware attacks that we encourage you to check out:
- Protect Against Ransomware as a Service Groups: Basic to Advanced Steps
- What’s Trending in AI Cybersecurity Threats? 5 Tactics to Be Aware of
- Defending Your Business Against the Rising Tide of AI Cybercrime
- Stop Ransomware: Your Checklist to Mitigate Malware Attacks
- Prevent Ransomware, Bust These 4 Myths

SQL Injections
An SQL injection is a form of attack cybercriminals use to execute malicious SQL code in a database. Putting it in simpler terms, SQL code is a language to communicate to computers. You can use it to tell the computer what you want it to do, like find some information or create a table, for example. Cybercriminals use this code to change, steal or delete data.
SQL injection attacks pose a serious risk to any website that relies on a database because they can cause irreversible damage.
Malware
Malware is software that is intended to harm computer systems. It can take the form of viruses, Trojans or spyware. Malware can be used to steal personal information, corrupt files and even disable systems. It’s important to be cautious when interacting with suspicious messages or links to protect yourself from potential cyber threats like malware.
Small Businesses Are Just as Susceptible to Cyber Risks
The media doesn’t typically report attacks on small businesses. They focus on the big fish with data breaches, but according to a recent report, 43% of all cyberattacks target small businesses.
No business is immune to cyber threats, which is why it’s so important to understand the WHY behind protecting your organization. Now, let’s talk about the incident response plan we promised you.

How to Improve Your Cyber Incident Response Plan
You should feel confident about your level of preparedness if you were ever to face a cybersecurity breach, a natural disaster or a system failure. If you aren’t feeling so confident, then this portion of our blog will steer you in the right direction.
This information is here to serve as a resource to enhance your plan simply and straightforwardly. So, let’s dive in and make sure you’re ready for whatever comes your way.
Best Practices for Effective Cyber Incident Response Planning
To be well-prepared for any incident, we’ve established a list of best practices:
Identify and prioritize critical data and assets
Knowing precisely what resources you have helps you allocate them efficiently during an incident, saving time and minimizing overall damage.
Establish a dedicated team
A cohesive and well-trained team with clearly defined roles can work together to ensure an efficient and effective response.
Conduct regular trainings
Regular training helps keep your team informed of the latest techniques and procedures, ensuring they can handle any situation with confidence.
Implement continuous monitoring
Continuous monitoring systems can detect incidents early and take action before they escalate, potentially saving your organization from significant damage.
Establish clear communication channels
Clear communication channels within your team and with external stakeholders ensure that everyone is on the same page during the response, minimizing confusion and errors.
Develop a system to categorize incidents
Categorizing incidents based on their severity and impact ensures that you can respond appropriately to each incident, minimizing long-term damage to your organization.
For more reading on incident response plans, we have the following resource for you to dive deeper:
How Prime Secured Can Help with Your Cybersecurity Response Plan:
If you’re unsure about how to develop an incident response plan, we offer several steps to assist you:
- Custom Incident Response Plan: We’ll tailor an incident response plan that meets your specific goals and addresses your unique challenges.
- Identify Vulnerabilities: Through risk assessments, we’ll pinpoint vulnerabilities and prioritize your incident response planning. Additionally, we offer a complimentary network assessment that you can utilize at your convenience.
- Build & Define Roles: We’ll help you establish a fully equipped incident response team, ensuring that each member understands their specific role.
- Advanced Security Strategies & Technologies: We’ll recommend and implement cutting-edge security technologies to enhance your detection capabilities.
- 24/7 Firewall & Endpoint Monitoring: We’ll set up continuous monitoring to swiftly detect and address potential security incidents.
- Compliance with Standards: We’ll ensure your incident response plan adheres to all legal and regulatory requirements.
- Post-Incident Analysis: After an incident, we’ll provide analysis to refine your response plans based on the lessons learned.
Take control of your cyber incident response plan
Don’t wait to become a victim of a security breach. Our team has years of experience and expertise to ensure the safety of your data. Take charge of your incident response plan now by scheduling a no-obligation consultation with our team of experts.




