Email Extortion Scams Are Becoming Even More Personal
In the shadowy corners of the internet, cybercriminals are constantly devising new ways to exploit our fears and vulnerabilities. As of September, a particularly unsettling email extortion scam has emerged, targeting unsuspecting individuals with a chilling level of personal detail. This isn’t just another spam campaign—it’s a sophisticated attack designed to panic you into compliance.
How the Email Scam Works
It begins with an alarming email containing an attached PDF. The subject line may read something like:
“I know visiting [insert your neighborhood] would be a more convenient way to reach in case you don’t act”
Attached is a PDF containing a Google Maps screenshot of your home or neighborhood, accompanied by an ominous message. The scammer claims to know everything about you, alleging they’ve been watching your every move through spyware supposedly planted on your device during a visit to a “questionable” website.
The extortionist states they have access to your email, contacts, and social media accounts. Even more disturbingly, they claim to have been recording compromising photos and videos of you in the privacy of your own home.
Below is an example from a Reddit user who received such an email:

What do they want in return for keeping your private moments confidential? Unsurprisingly, the answer is money.
How Are Criminals Gathering Your Information?
The sheer fear induced by this scam lies in the fact that the scammers seem to know personal details, such as your home address. But how do they get this information if the threat isn’t real? The answer: data breaches.
By leveraging data that’s already been stolen through breaches, scammers elevate their scare tactics, creating sophisticated and frightening extortion emails. As data breaches become increasingly common, expect more of these scams to emerge—and they’re likely to become even more convincing.
"Unfortunately attacks are only going to become more commonplace and more sophisticated, especially with the growth of AI. We also need to be more thoughtful about the information that we share publicly that could later be leveraged by a threat actor."
Justin Ekstein, Solution Engineer, Prime Secured
What Should You Do If You Receive This Email?
- Do not respond. Engaging with the scammer only signals that you’re frightened or concerned, making you a more attractive target.
- Do not pay any money. The purpose of the scam is to scare you into paying. It’s a bluff, and complying will only encourage further extortion attempts.
- Report the email. If you use Gmail, report the email as spam by clicking the warning icon.
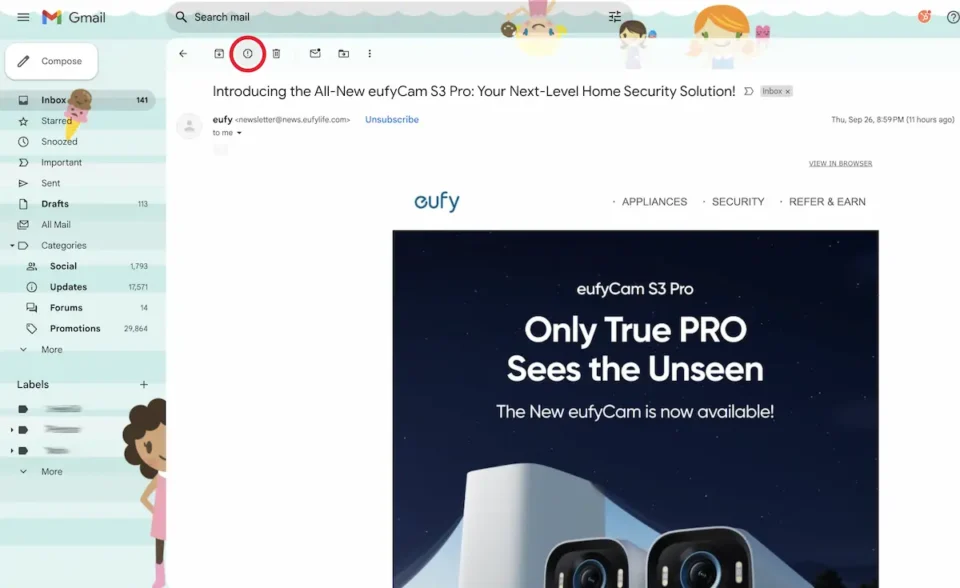
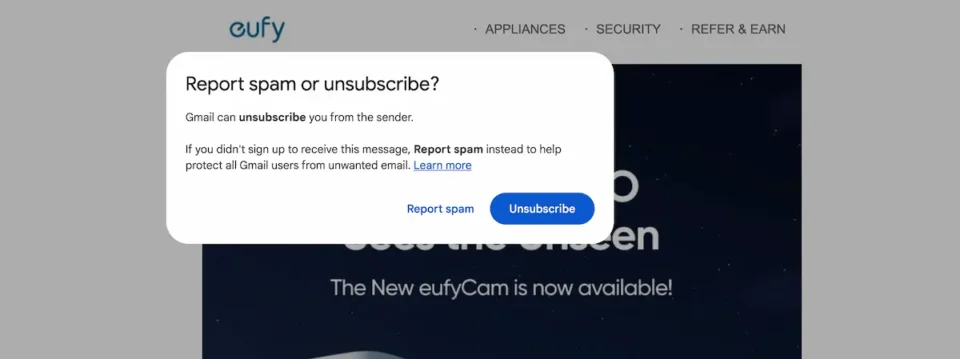
For Microsoft users, you can report the email by clicking the shield icon located in the tool ribbon.
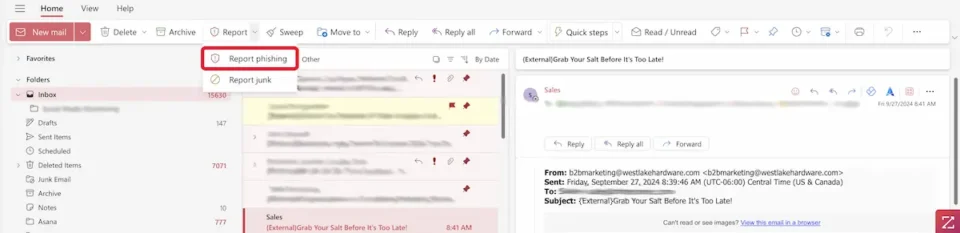
How Businesses Can Protect Their Employees & Customers
- Use an email quarantine system. A quarantine system will automatically identify and isolate spam and phishing emails, preventing them from reaching users’ inboxes.
- Maintain a strong cybersecurity posture. Conduct regular network assessments, penetration testing, and ensure hardware, software, and firmware are up to date. Proactively protecting your systems reduces the risk of data breaches that make scams like this possible.
- Education and awareness. As we’re doing here today, keep employees and customers informed about emerging scams and online threats.
- Monitor dark web for data leaks. Invest in dark web monitoring services to detect if your business or customer data appears in underground marketplaces. Early detection can help you respond swiftly to potential threats.
- Establish a clear incident response plan. Prepare for the worst by creating a detailed plan for responding to potential data breaches or scam attempts. This should include steps for containment, assessment, and communication with affected parties.
- Use a password manager. Another step we would suggest is to ensure that you are using a reputable password manager for both personal and business use. It can help to reduce the reach of breaches as well as the effectiveness of these campaigns.
We've Got Your Back
We want our customers and subscribers to know that we’re here to support you. If you’d like to learn more about how we can help improve your business’s cybersecurity posture and protect sensitive customer data, reach out to us for a free network assessment.
With the trending nature of cybercrime, cybersecurity isn’t just an IT issue—it’s a business imperative.




