Understanding What’s on Your Network- Why is it so Important?
Do you know the current state of your IT environment? Maybe you were the one to choose your networking hardware and platforms, or inherited an undocumented setup, or rely on a service provider who hasn’t shared much about your network’s status. If either of these scenarios ring true, this topic is for you. We’re going to cover what a network assessment includes, how it’s conducted, the information you can gain, and how to request one.
There are numerous reasons. You may possess hardware that is outdated and no longer supported, posing a security threat and affecting user experience. Third-party patches might require updates to close potential backdoors for hackers. It’s possible to have accounts of former employees that are still active and unknown to you. Some employees may not adhere to password policies, making them vulnerable to hacking attempts. Ultimately, it’s vital to be aware of your cybersecurity posture to protect your business effectively.
"We've performed assessments on several environments, where the client felt that their network was in good hands. What we've found is that some of the most basic blocking and tackling is missed - things that you just assume are happening and being done the right way. These are the things that can hurt the most when exploited."
Justin Ekstein, Solution Engineer
What Information is Collected in a Network Assessment?
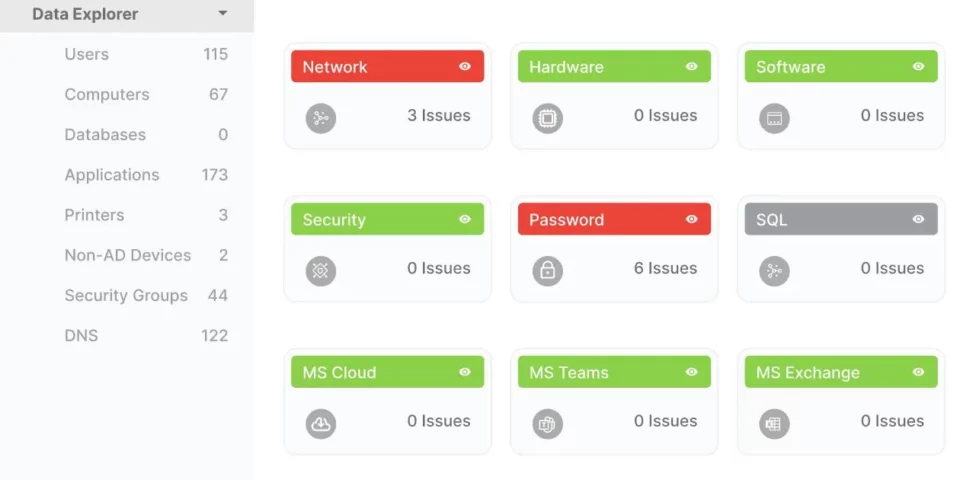
A network assessment evaluates:
Overall Network Architecture: This includes the design and layout of your network, focusing on scalability, reliability, performance, and security.
Hardware & Software Inventory: A detailed list of all your network’s physical and software assets, aiding in asset management, maintenance planning, and ensuring software compliance.
Cybersecurity Posture: An examination of your network’s security measures, including password policies, active and deactivated users, to gauge your cybersecurity health.
Performance Analysis: Insights into data transmission speed, application performance, and bandwidth utilization, which affect user satisfaction and productivity.
Compliance with Standards and Policies: Ensures your infrastructure adheres to industry security standards and internal policies, safeguarding your operations and legal standing.
An expert compiles this data into a comprehensive report, highlighting your overall risk and issues. For a glimpse at a detailed network assessment, download Prime Secured’s sample of a completed network assessment.
So, What Next?
With this data, managed service providers, like Prime Secured, can craft a custom plan for your business. This may include a technology roadmap for the next five years, outlining when to replace hardware or update software, helping you plan your technology budget and avoid unexpected failures.
Thinking About a Network Assessment?
Wondering about the process and time commitment? Our senior technical experts conduct assessments by:
- Planning & Scoping: Setting goals and timelines.
- Data Gathering: Collecting detailed information on your network.
- Vulnerability Scanning: Identifying security vulnerabilities.
- Performance Analysis: Assessing network efficiency and identifying bottlenecks.
- Compliance Check: Ensuring adherence to standards and policies.
- Reporting & Recommendations: Offering an overview of your network’s status & improvements.
We hope this information has been useful to you. When we initially meet with clients overwhelmed by managing their IT and cybersecurity, they’re dealing with a fragmented setup — one vendor for firewalls, another for helpdesk needs, with various components pieced together haphazardly. If this scenario resonates with you, we recommend starting with a network assessment as your first step.
Get started by booking your complimentary network assessment.
In addition to our sample network assessment report, we want to provide you with these additional resources:
- In 2023 we conducted over 30 network assessments on organizations with an IT provider. We found a lot of gaps where organizations thought they were covered. You can access those results here.
- Stressed about switching providers? Download our guide on how we make switching your IT partner easy.
- Looking to understand in general how an IT provider can save you time and money. Read, How IT Providers Simplify Technology Budgeting for Small Businesses