2025 Top Cyber Threats & Your Plan for Prevention
Cybersecurity is your top priority and with cyber threats evolving and deploying faster and faster, it can feel like a 200 lb. weight on your chest. You are responsible for protecting your employee and customer data, and that responsibility feels like disaster is looming right around the corner.
Let’s alleviate some of the dread.
We’re covering new trends our IT experts are seeing, helpful tips, and tools to empower you to enhance your organization’s cybersecurity posture.
#1 Zero-Day Ransomware Attacks
Ransomware a type of malware that locks your files or systems demanding a form of payment, usually in cryptocurrency, to return data, is one cyber-attack that we are seeing advance in ways that are quite unsettling.
Prime Secured cybersecurity expert Justin Ekstein explains:
“It used to be that from the time you would click a link in an email to the time that your systems would get encrypted, it was usually about a month. But now, in the last six months, that timeline has shrunk to under four hours.”
That’s a significant increase and leaves you with a very small window to respond. We recommend implementing a proactive approach to preventing zero-day ransomware attacks.
Plan to Protect Against Ransomware
- Implement Defense-in-Depth Approach: Use a combination of antivirus software, firewalls, and network monitoring tools.
- Backup Regularly: Ensure your data is backed up securely and test your restoration process regularly.
- Invest in Security Operations Centers (SOCs): SOCs can monitor your entire IT environment and identify suspicious activity in real time.
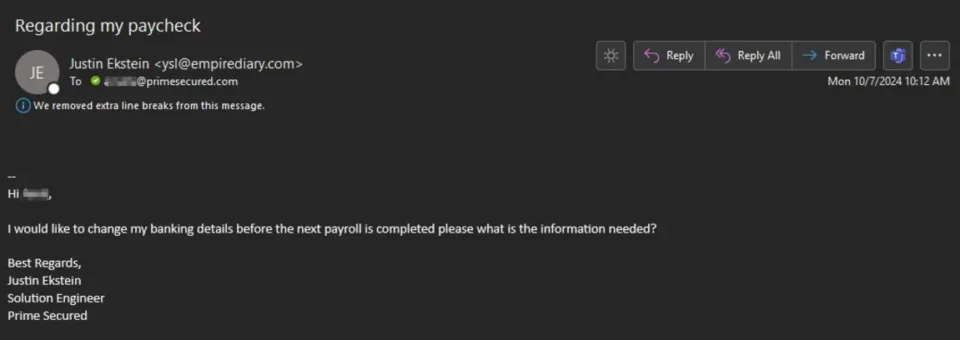
#2 Hard to Spot Email Spoofing
AI has given everyone a leg up. Previously, cyber criminals had to manually craft phishing emails, often hindered by poor writing skills. Now, they can use AI to mimic the writing styles of individuals or organizations, leveraging social media footprints to make their messages even more convincing. Basic email security tools lack the intelligence needed to catch this type of spoofing.
AI has given everyone a leg up. Previously, cyber criminals had to manually craft phishing emails, often hindered by poor writing skills. Now, they can use AI to mimic the writing styles of individuals or organizations, leveraging social media footprints to make their messages even more convincing. Basic email security tools lack the intelligence needed to catch this type of spoofing.
Tips to Protect Against Email Spoofing
- Use Advanced Email Security Tools: Invest in systems that can analyze email headers and detect unusual patterns. Mail Protector is one option that our team recommends.
- Educate Your Team: Train employees to recognize the signs of email spoofing, such as unusual requests, especially where personal details are involved. Educate them on trending email attacks.
- Adopt Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring additional verification before granting access to sensitive systems. Be aware that the most secure form of MFA is through an authenticator app and the least secure form is SMS messaging.
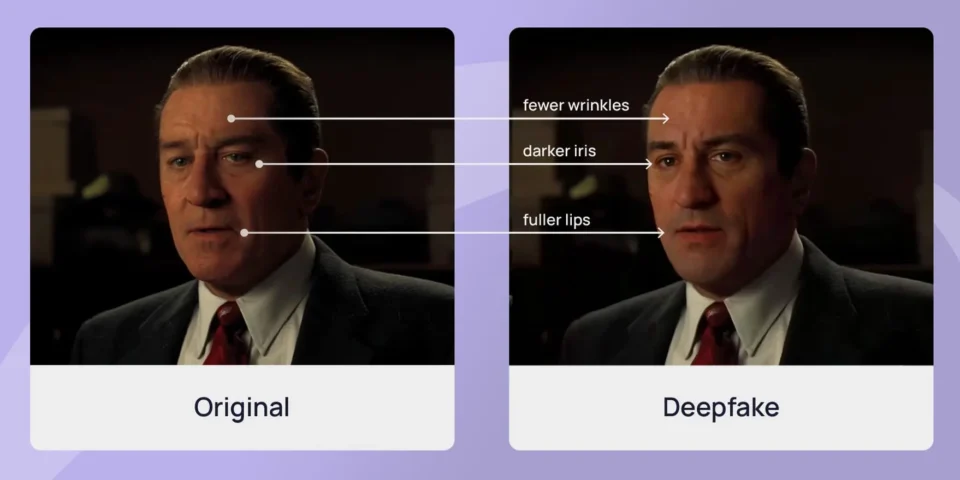
#3 Is it Real or a Deepfake?
Example of Deepfake Risks
Ekstein points out that deepfakes have been leveraged to gain access to bank accounts or to wire money to someone. Some institutions are implementing in-person or call back requests as a form of authentication.“I spoke with a bank that encountered an issue where audio was manipulated to sound like a client requesting a wire transfer from their account. Due to the unusual nature of the request, the bank felt something was off. Thankfully, they caught the incident. Moving forward, they now require callers to hang up and call back using the number on file to verify their identity or encourage clients to visit in person whenever possible.”
How to Protect Against Deepfakes
- Verify Identities: For critical transactions, implement multi-step verification processes, such as callback procedures or in-person confirmations.
- Limit Public Information: Be mindful of the personal details and videos shared online, which attackers can use to create convincing deepfakes.
- Educate Employees: Train your team to recognize the signs of deepfake technology and implement policies to reduce risks.
- Protect Users: Emphasize the importance of protecting users from cyber threats through proactive measures such as AI-powered threat protection and robust security solutions that adapt to the remote and distributed nature of the modern workforce.
Key Takeaways for Enhancing Your Cybersecurity Strategy
-
Start with Defense-in-Depth
No single solution can protect your business from all cyber threats. A defense-in-depth approach, which involves multiple layers of security is needed for complete protection. This includes endpoint security, network monitoring, and backup and restore tests Include These in your Multi-step ApproachFollow Key Cyber Hygiene Practices
- Security Operations Centers (SOCs): SOCs provide real-time monitoring and can correlate data across your IT environment to identify threats.
- Cloud Security: With more businesses relying on platforms like Office 365, SharePoint, and Google Drive, monitoring cloud environments is essential.
- Endpoint Protection: Use advanced tools to protect devices from malware and unauthorized access.
- Network Segmentation: Network segmentation is a critical component in enhancing security within a digital infrastructure. It helps eliminate lateral movement by isolating breaches, thereby defending against insider threats and minimizing potential damage caused by unauthorized access.
- Update Regularly: Keep all software and systems up to date to address vulnerabilities.
- Password Management: Use strong, unique passwords and a password manager to store them securely.
- Enable Multi-Factor Authentication (MFA): MFA significantly reduces the risk of unauthorized access.
-
Implement an Employee Cyber Training Program
Your employees are your first line of defense but also your weakest link. They won’t always get it right, which is why an educated workforce is critical to prevention. With 45% of ransomware attacks starting with phishing emails, implementing regular training and updates on trending scams equips your team to better defend against threats. How to implement an effective program:
- Conduct regular phishing simulations: Test employees’ responses to phishing attempts and provide immediate feedback and additional training for improvement.
- Provide ongoing education: Share updates on the latest cyber threats and scams, ensuring employees are aware of new tactics used by attackers.
- Gamify training efforts: Use incentives or recognition to encourage engagement and reward high-performing employees who demonstrate strong security practices.
-
Review Your Processes & Procedures
Ask yourself: Do you have a method for verifying client or staff identities to avoid falling victim to deepfakes? Do you know how to respond if one is spotted? Are policies like multi-factor authentication (MFA) enforced across your organization? Regular reviews ensure you remain proactive when cyber threats are constantly improving. How to refine your processes:
- Establish verification protocols: Require staff to confirm identities through secure methods, such as callback verifications or in-person confirmations when dealing with sensitive requests.
- Create a response plan for deepfakes: Define steps for identifying and addressing suspected deepfakes, including escalation procedures and communication strategies.
- Enforce MFA across all systems: Mandate multi-factor authentication for all users to add an extra layer of security against unauthorized access.
Justin Covers Ransomware, Email Spoofing, Deepfakes and more
Build Up Your Defenses with a Managed IT Provider
A powerful cybersecurity plan covers a lot of avenues, as we discussed above. It can be difficult and overwhelming to be tasked with taking them all on yourself. In situations like this, selecting a company to partner with for cybersecurity removes the pressure of going it alone. A managed services provider will have a dedicated team that specializes in each aspect of cybersecurity, leading to a holistic prevention strategy.
Curious to learn more about how a partnership could work? Contact our team at Prime Secured, where IT experts like Justin Ekstein can handle your cybersecurity measures while you have peace of mind knowing your employees’ and customers’ data is safe.
Disclaimer: AI was utilized for proofreading and topic research, this post otherwise was written by a human.